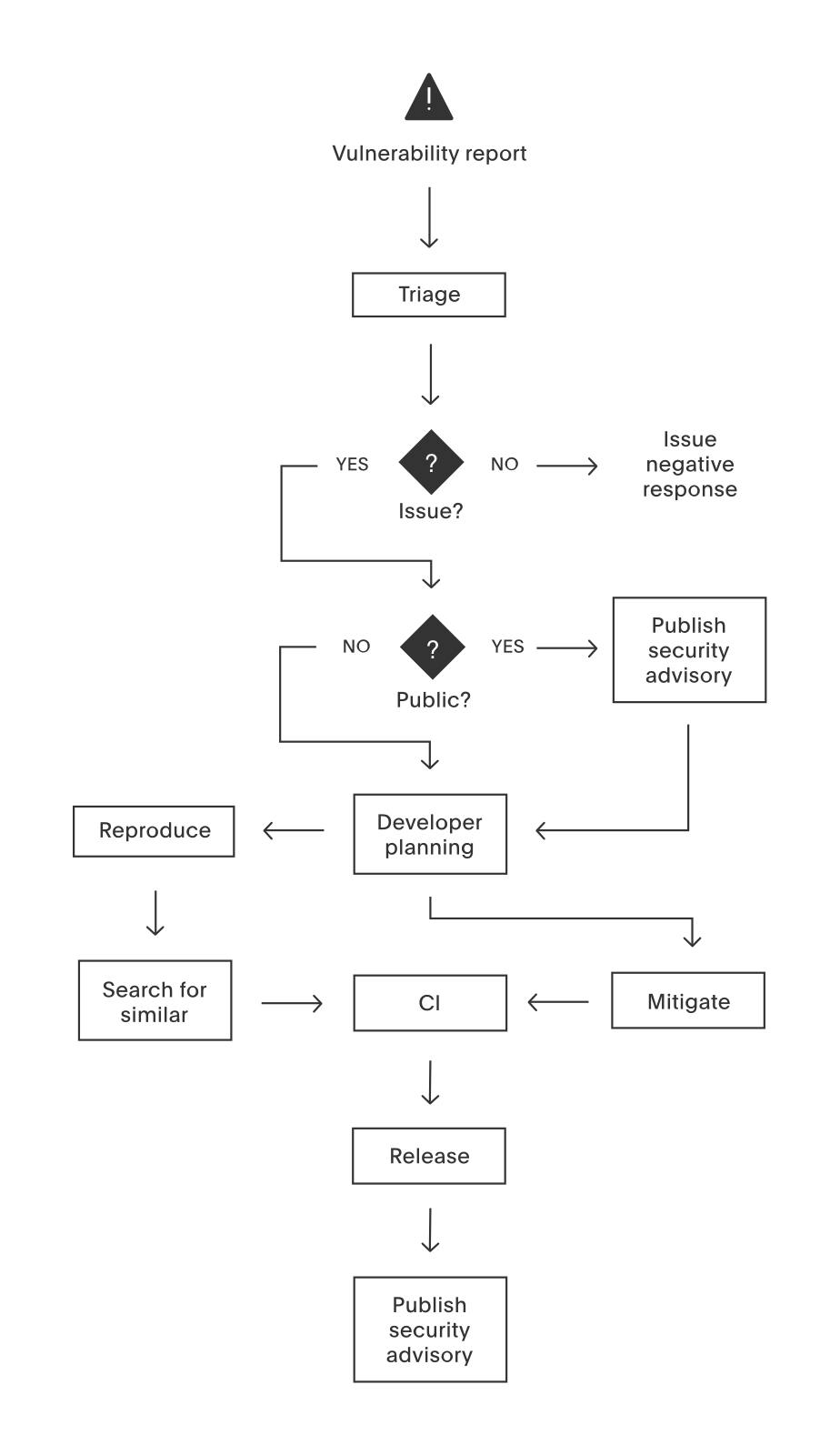
Issues which impact (in a way which can be used by an attacker) the Confidentiality, Integrity or Availability (CIA) of installations are considered to be security issues. At this point severity is not considered: if it impacts one of CIA, then it’s a security issue.
Security issues are prioritized by severity using CVSSv3 scoring:
- Vulnerabilities are labeled “Low” severity if they have a CVSS base score of 0.0-3.9.
- Vulnerabilities will be labeled “Medium” severity if they have a base CVSS score of 4.0-6.9.
- Vulnerabilities will be labeled “High” severity if they have a CVSS base score of 7.0-8.9.
- Vulnerabilities will be labeled “Critical” severity if they have a CVSS base score of 9.0-10.0.
These map to turnaround times as follows:
- Low: next maintenance release
- Medium/High: maintenance release with seven days
- Critical: 48 hours for patch/mitigation
PSIRT can raise the priority to Critical in response to exploitation in the wild, public disclosure, etc.